Page 12 - TNR-V02N1
P. 12
• Transfer the risk > The aim is to ensure the data in custody would be
Get cybersecurity insurance coverage and hope that reasonably safe from attacks, while remaining functional and
they will absorb the cost if the risk is realized. usable. There must be a balance. Over-securing could either
• Reduce the risk > get outside cybersecurity help from make the data unusable or simply cost more than the value
a specialized outsource company to harden the IT being protected.
infrastructure.
• Hedge against the risk > Reduce and transfer the Conclusions
risk, by implementing both (4) and (5) - the “belt and In 1736, Benjamin Franklin helped create the “Union
suspenders” approach. Fire Company” in Philadelphia. This became a model for
subsequent modern municipal fire departments. On the
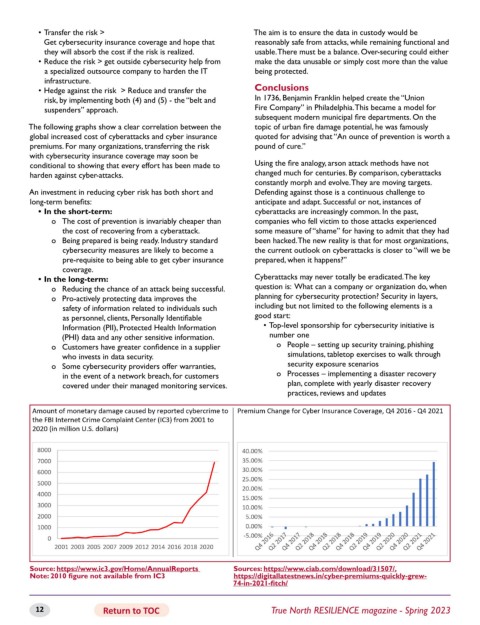
The following graphs show a clear correlation between the topic of urban fire damage potential, he was famously
global increased cost of cyberattacks and cyber insurance quoted for advising that “An ounce of prevention is worth a
premiums. For many organizations, transferring the risk pound of cure.”
with cybersecurity insurance coverage may soon be
conditional to showing that every effort has been made to Using the fire analogy, arson attack methods have not
harden against cyber-attacks. changed much for centuries. By comparison, cyberattacks
constantly morph and evolve. They are moving targets.
An investment in reducing cyber risk has both short and Defending against those is a continuous challenge to
long-term benefits: anticipate and adapt. Successful or not, instances of
• In the short-term: cyberattacks are increasingly common. In the past,
o The cost of prevention is invariably cheaper than companies who fell victim to those attacks experienced
the cost of recovering from a cyberattack. some measure of “shame” for having to admit that they had
o Being prepared is being ready. Industry standard been hacked. The new reality is that for most organizations,
cybersecurity measures are likely to become a the current outlook on cyberattacks is closer to “will we be
pre-requisite to being able to get cyber insurance prepared, when it happens?”
coverage.
• In the long-term: Cyberattacks may never totally be eradicated. The key
o Reducing the chance of an attack being successful. question is: What can a company or organization do, when
o Pro-actively protecting data improves the planning for cybersecurity protection? Security in layers,
safety of information related to individuals such including but not limited to the following elements is a
as personnel, clients, Personally Identifiable good start:
Information (PII), Protected Health Information • Top-level sponsorship for cybersecurity initiative is
(PHI) data and any other sensitive information. number one
o Customers have greater confidence in a supplier o People – setting up security training, phishing
who invests in data security. simulations, tabletop exercises to walk through
o Some cybersecurity providers offer warranties, security exposure scenarios
in the event of a network breach, for customers o Processes – implementing a disaster recovery
covered under their managed monitoring services. plan, complete with yearly disaster recovery
practices, reviews and updates
Source: https://www.ic3.gov/Home/AnnualReports Sources: https://www.ciab.com/download/31507/,
Note: 2010 figure not available from IC3 https://digitallatestnews.in/cyber-premiums-quickly-grew-
74-in-2021-fitch/
12 Return to TOC True North RESILIENCE magazine - Spring 2023