Page 10 - TNR-V02N1
P. 10
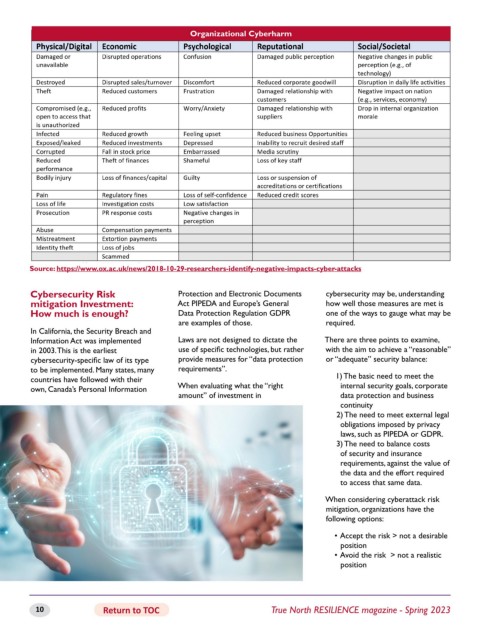
Organizational Cyberharm
Source: https://www.ox.ac.uk/news/2018-10-29-researchers-identify-negative-impacts-cyber-attacks
Cybersecurity Risk Protection and Electronic Documents cybersecurity may be, understanding
mitigation Investment: Act PIPEDA and Europe’s General how well those measures are met is
How much is enough? Data Protection Regulation GDPR one of the ways to gauge what may be
are examples of those. required.
In California, the Security Breach and
Information Act was implemented Laws are not designed to dictate the There are three points to examine,
in 2003. This is the earliest use of specific technologies, but rather with the aim to achieve a “reasonable”
cybersecurity-specific law of its type provide measures for “data protection or “adequate” security balance:
to be implemented. Many states, many requirements”.
countries have followed with their 1) The basic need to meet the
own, Canada’s Personal Information When evaluating what the “right internal security goals, corporate
amount” of investment in data protection and business
continuity
2) The need to meet external legal
obligations imposed by privacy
laws, such as PIPEDA or GDPR.
3) The need to balance costs
of security and insurance
requirements, against the value of
the data and the effort required
to access that same data.
When considering cyberattack risk
mitigation, organizations have the
following options:
• Accept the risk > not a desirable
position
• Avoid the risk > not a realistic
position
10 Return to TOC True North RESILIENCE magazine - Spring 2023